Over the last few years, attacks on websites have increased at an alarming rate. We are at the point now where anywhere from 30,000 to over 100,000 websites are being hacked every single day on average.
While this is a scary statistic in of itself, even more frightening is just how easy it is for these attackers to gain access to websites through various malicious means. The reason being is that website owners are either unaware of vulnerabilities that exist within their websites, or take website security as an afterthought, and leave them exposed to such attacks, due to lack of planning and protection. As detailed in a previous blog post here, we at GreyBox creative take website security seriously, and can help your organization stay safe when it comes to your website.
One crazy story that we wanted to share, because it was just too scary not to tell the tale, happened about 6 months ago. We had just taken over web security for one of our clients that did take web security seriously. Their previous web security team assured them that their website was safe, and those vulnerabilities inherent within WordPress, and the plugins that the website was using, were being patched, and updated. However, when we took a look “under the hood” of the website, we found that to not be the case whatsoever.
As is typical with the website security service that we offer, we first went in, created multiple backups, and created a copy of the website in question to one of our development servers before we dug in deep and starting shoveling our way through the thick of things. Once copied over to one of our development servers, we then took a look at the plugins, as well as the WordPress core, to see if any of them were out of date, and needed updating, and what we were presented with was shocking to say the least:
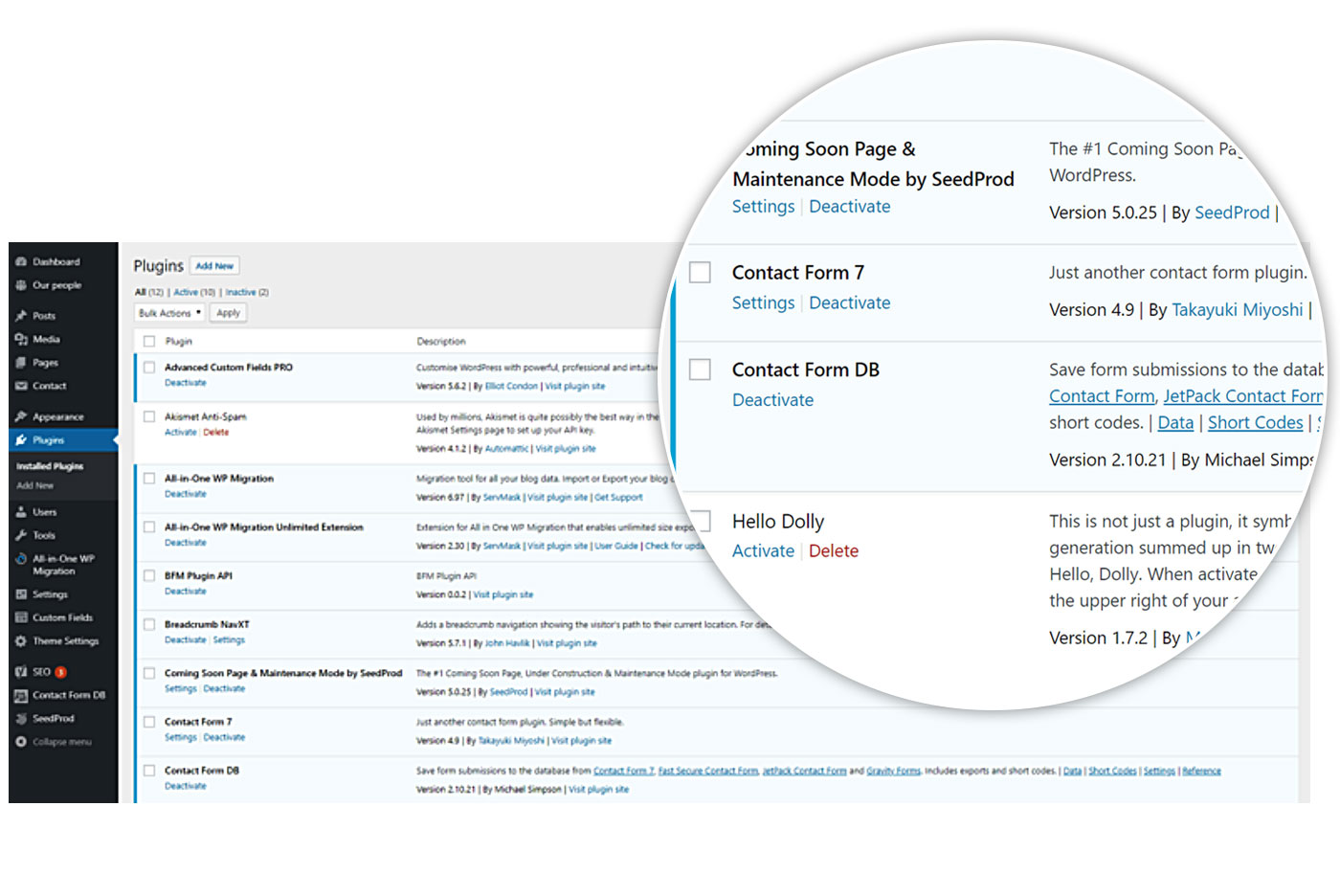
As you can see from the above, WordPress reported that all plugins are fully up to date. However, this is far from the truth. The easiest way to tell is by looking at one of the plugin versions, for example “Contact Form 7” which reports as using version 4.9, and being “up to date”. When you compare that to Contact Form 7’s release log here you can see that version 4.9 was released on August 18, 2017. The next version of Contact Form 7, version 4.9.1 was released on October 31, 2017, or just over a month after version 4.9. What this means is that the plugin was almost 2 years out of date while the previous web security team ensured the client that the plugins were being updated, and the client was also re-assured that this was the case, when they logged in to the backend of their website to manage it. As detailed in previous blog posts of ours, outdated plugins, especially really old versions are one of the most common ways that hackers can gain unauthorized access to WordPress and other CMS based website. Given what we have described in the above, and armed with this knowledge, you should be able to paint a picture of how frightened we were to see this. So, the question is, how did this happen, and why?

As for the how, after some deep digging into the code of the website, we found that the previous security team put in place some custom code that was designed specifically to block WordPress from being able to determine which plugins, and also WordPress core itself, were out of date and needed updating.
This resulted in WordPress thinking that everything was up to date, and reporting it as such to the client, basically giving them the false impression that everything was okay. This is a very bad thing, because for one it makes updating plugins and WordPress a somewhat dubious endeavor due to not knowing when new updates are released, and hence not knowing when an update needs to be pushed live. The second aspect of this, which we will touch on a bit more on below, is that it eliminates a layer of transparency, and essentially deceives the end-client in terms of the work which is being done.
As for the why, it is our personal opinion that any time this level of effort is put into hiding transparency of security related work; it is that the work is simply not being done. As for the facts, we know that the previous firm was engaged to specifically secure the website, with the directive that frequent updates be made to WordPress and it’s plugins. We also know that prior to us taking over security, the previous firm had been engaged for over a year. The only conclusion that can be had, based on the facts, and the Contact Form 7 plugin (any many others for that matter) being outdated by over 2 years, is that the work to secure the website by the previous firm was simply not done.
All of this is to say that when deciding who you work with in securing your website, you should always ask for a minimum level of transparency in terms of what is being done, as well as a way to check and ensure, from at least a high level, and at most a granular level that what is required to ensure the safety and security of your website is being done.
GreyBox Creative has extensive knowledge and experience when it comes to website security, and we are more than happy to discuss with you any points or concerns you have with regards to website security. We are always an email or a quick call away. If you would like to discuss this with us, please click here to send us an email.
